Achieve Cybersecurity Compliance Effortlessly!
-

Phase 1
You will receive an email with a workbook to identify your assets and risk (threats and vulnerabilities). You will also take the assessment if you have not already done so. After you complete your homework, we will schedule a 2-hour session to install BitDefender Gravity Zone Business Security Endpoint Detection and Response and verify/configure security settings on all applicable devices. If needed, we will install Trustifi for Encrypted Email & Attachments with password/MFA controls.
NOTE: You will have homework
-

Phase 2
Our next 2-hour session will be to discuss how you collect, transmit, and store information. We will find ways to make sure it is secure and compliant with all applicable regulations. We will work together to make sure you are using unique accounts, strong passwords and Multifactor Authentication where possible. We will also look at how you limit employee access to information, backup information, apply security patches, and ensure your customers’ privacy.
NOTE: Depending on the extent of work needed to complete this it may require homework and/or a follow-up session.
-

Phase 3
You will receive draft Cybersecurity Policies for your industry as applicable. For example, Financial (IRS WISP), Healthcare (HIPAA Privacy and Security), Government Contractors (CMMC SSP & POAM).
We will also develop any other cybersecurity related policies you need including but not limited to Incident Response and Disaster Recovery Plan, Breach Notification Plan, Website Privacy Statement, Employee Conduct and Device Use Policies.
NOTE: This will require homework because you must review the documents.
-

Phase 4
The final session will be to hold training with you and your team to make sure everyone is aware of cybersecurity basics, and their role in security, your organizations expectations, and how to spot and respond to a phishing attack.
We will also provide guidance to repair your reputation after an incident occurs, mitigate damage to your customers, and provide guidance with ensuring response planning processes are executed during and after an incident.
NOTE: We will continue to monitor everything and provide support as needed for the length of the contract.
How does NIST CSF make you compliant?
Although primarily US-based, the National Institute of Standards and Technology Cybersecurity Framework (NIST CSF) has reached international application and is used by several organizations worldwide, and especially in Canada for IT compliance.
In August 2023, the U.S. National Institute of Standards and Technology released an updated Cybersecurity Framework with significant changes, including an emphasis on governance and supply chain risk management that align with Canadian legal requirements and regulatory guidance. The updated Framework will be an important benchmark resource for Canadian organizations of all kinds and sizes.
There are no "silver bullets" when it comes to cybersecurity and protecting an organization. For instance, "Zero-day" attacks exploiting previously unknown software vulnerabilities are especially problematic.
However, using the National Institute of Standards and Technology (NIST) Cybersecurity Framework (CSF) to assess and improve management of cybersecurity risks will put your organization in a much better position to identify, protect, detect, respond to, and recover from an attack, minimizing damage and impact.
NIST CSF will enable you to meet or exceed all government mandated cybersecurity regulations like HIPAA, GLBA, PCI-DSS, FINRA, SOX, CMMC, ITSG-33, ISO 27001, and many others.
Not just a software solution, it also uses governance, processes, and awareness
Enable long-term cybersecurity and risk management
A framework that keeps you compliant effortlessly
A framework that is flexible and easily adaptable regardless of size and type of your business
Scalable to grow as your business grows and is a valuable to build trust with your customers
Helps your organization achieve a global standard of cybersecurity
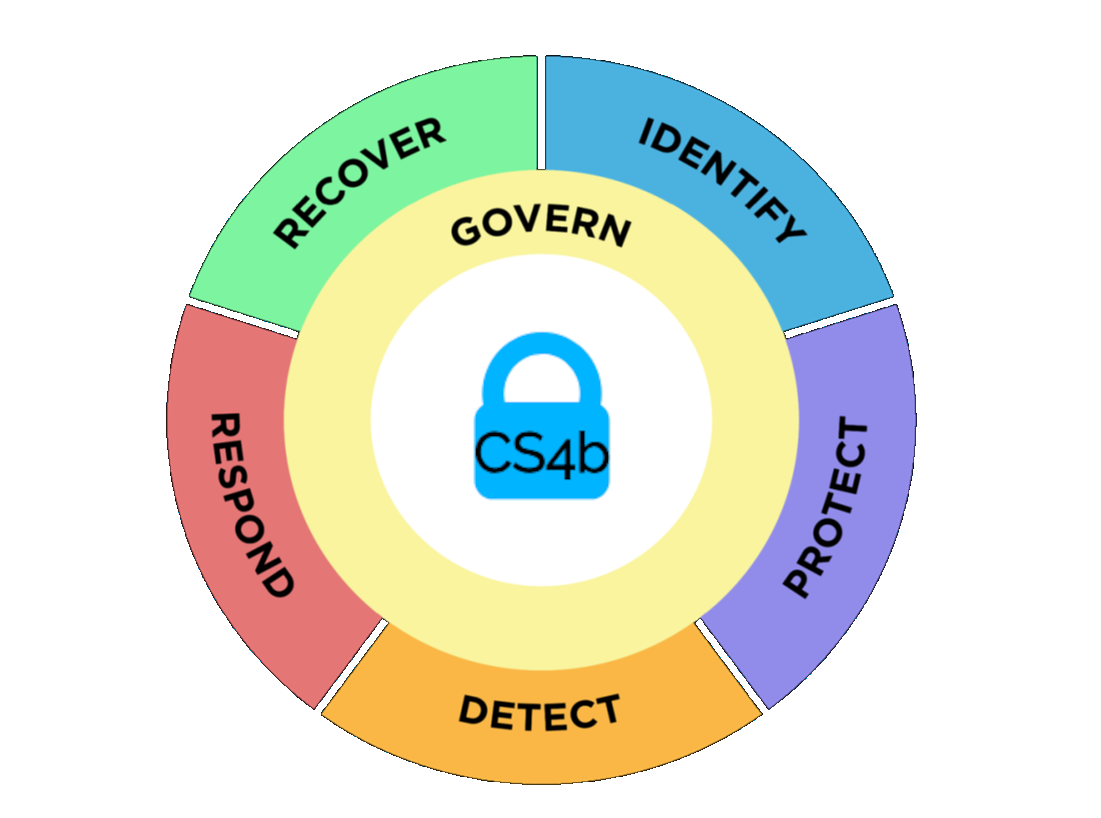
The NIST CSF 2.0 organizes basic cybersecurity activities at their highest level with these 5 functions.
-

Document your assets (hardware, software, people, and critical processes).
Assess the potential impact of a total or partial loss of critical business assets and operations.
Assess cybersecurity risks posed by suppliers and other third parties before entering into formal relationships.
-

Assessment Questionnaire
Identify and control who has access to your business information
Require individual user accounts for each employee.
Create Cybersecurity Policies (HIPAA Security & Privacy, GLBA/IRS WISP, CMMC SSP & POAM, PCI-DSS, Company Cybersecurity Policy)
-

Limit employee access to data and information
Install and activate software and hardware firewalls on all your business networks
Secure your wireless access point and networks
Dispose of old computers and media safely
Train your employees
-

Advanced Threat Security
Email Security and Antispam
Exploit Defense
Full Disk Encryption
Network Attack Defense
Patch Management
Web Content Control
Web Threat Protection
-

Managed Endpoint Detection and Response
Develop Response Plans for disasters, data breaches, and information security incidents
Repair your reputation
Mitigate damages to your customers
Prioritized Alerts Investigation
-

Full backups and incremental backups of important business information and customer data
Consider cyber insurance
Make improvements to processes, procedures, technologies
Business Continuity Plan