Service provided by Cybersecurity4biz
-

Risk Management
Assess the impact of losing critical business assets or operations.
Evaluate the need for cybersecurity insurance.
Identify and manage cybersecurity risks posed by third parties, like suppliers or contractors.
Implement a Risk Management Framework tailored to your business.
-

Policy and Compliance
Create customized cybersecurity policies for:
Financial services (IRS WISP compliance).
Healthcare (HIPAA Privacy and Security).
Government contractors (CMMC SSP & POAM).
Verify compliance with state consumer data privacy laws.
Develop a website privacy policy for data collection practices.
-

Training and Awareness
Conduct Cybersecurity Awareness Training for your team.
Phishing Awareness – How to spot and avoid scams.
Password Management – Strong passwords and MFA.
Device Security – Securing computers, phones, and networks.
Data Protection – Safeguarding sensitive information.
Software Updates – Importance of timely patching.
-

Technical Security Services
Configure secure router, network, and firewall settings.
Ensure proper security settings on computers and mobile devices.
Implement tools like Trustifi for encrypted emails and attachments with MFA.
Configure Full Disk Encryption for devices.
Automate patch management to keep systems updated.
-

Data and Access Management
Data and Access Management is the process of ensuring that the right individuals have the appropriate access to the right data at the right time, while protecting sensitive information from unauthorized use.
Help track and manage inventory of hardware, software, and critical information.
Create processes to limit employee access to sensitive data and information.
Set up individual user accounts for employees.
-

Incident Management
Develop response plans for disasters, data breaches, and security incidents, including:
Breach Notification Plan.
Incident Response Plan.
Disaster Recovery Plans.
Guide you through reputation management after incidents.
Assist in mitigating damages to customers during and after an attack.
Provide prioritized alert investigations and real-time response.
-

Threat Monitoring and Protection
Deploy BitDefender GravityZone for endpoint security against malware, ransomware, and phishing attacks.
Monitor emails for phishing and malicious attachments.
-

Backup and Recovery
Guide the creation of full and incremental data backups.
Develop a Business Continuity Plan to ensure operational resilience.
Offer recommendations for improving processes, procedures, and technologies post-recovery.
-

Device and Media Management
Securely disposing of old computers and media A. by deleting and overwriting the file directory or by reformatting the drive where they were housed following the NIST 800-88 Data Wipe Method or destroying the drive disks rendering them inoperable if they have reached the end of their service life.
-

FTC GLBA Safeguards Rule
Conducting risk assessments, developing and enforcing security policies, and deploying both technical and physical safeguards to protect customer financial information. Conduct employee training, monitoring systems, access controls, encryption, and incident response plans. Regular reviews and updates ensure ongoing compliance and the protection of sensitive data.
-

HIPAA Gap Assessment
A HIPAA gap analysis is a good tool and highly recommended to determine if compliance with the privacy, security, and breach notification rules of the HIPAA regulations have been met or where the organization comes up short.. This assessment involves reviewing current compliance against HIPAA Security Rule requirements, identifying vulnerabilities, and providing recommendations.
-

CMMC 2.0
Conducting gap assessments, creating action plans, and aligning with the required security practices outlined in NIST SP 800-171. Providing employee training, policy development, and preparation for third-party audits, ensuring organizations are ready to protect sensitive information and meet DoD requirements effectively.
-

IRS Written Information Security Plan (WISP)
WISP is a comprehensive plan required for tax preparers and eFilers that outlines and explains the policies, protocols, procedures, and systems your company or organization utilizes to protect the sensitive personal information you collect, manage, and maintain about your clients, customers, benefactors, or patients.
-

PCI-DSS Security Assessment Questionnaire
PCI-DSS (Payment Card Industry Data Security Standard) compliance is a set of security standards designed to ensure that organizations handle credit card information securely. It outlines requirements for protecting cardholder data, including encryption, access control, and regular system monitoring. The PCI-DSS Self-Assessment Questionnaire (SAQ) is a tool used by organizations to assess their compliance with these standards.
-

State Consumer Protection Laws
State consumer privacy laws in the U.S. vary widely but generally aim to protect personal information from misuse by businesses. These laws require companies to disclose their data collection practices, give consumers the right to access, delete, or opt out of the sale of their data, and implement safeguards to protect personal information. Notable examples include the California Consumer Privacy Act (CCPA) and the Virginia Consumer Data Protection Act (VCDPA.
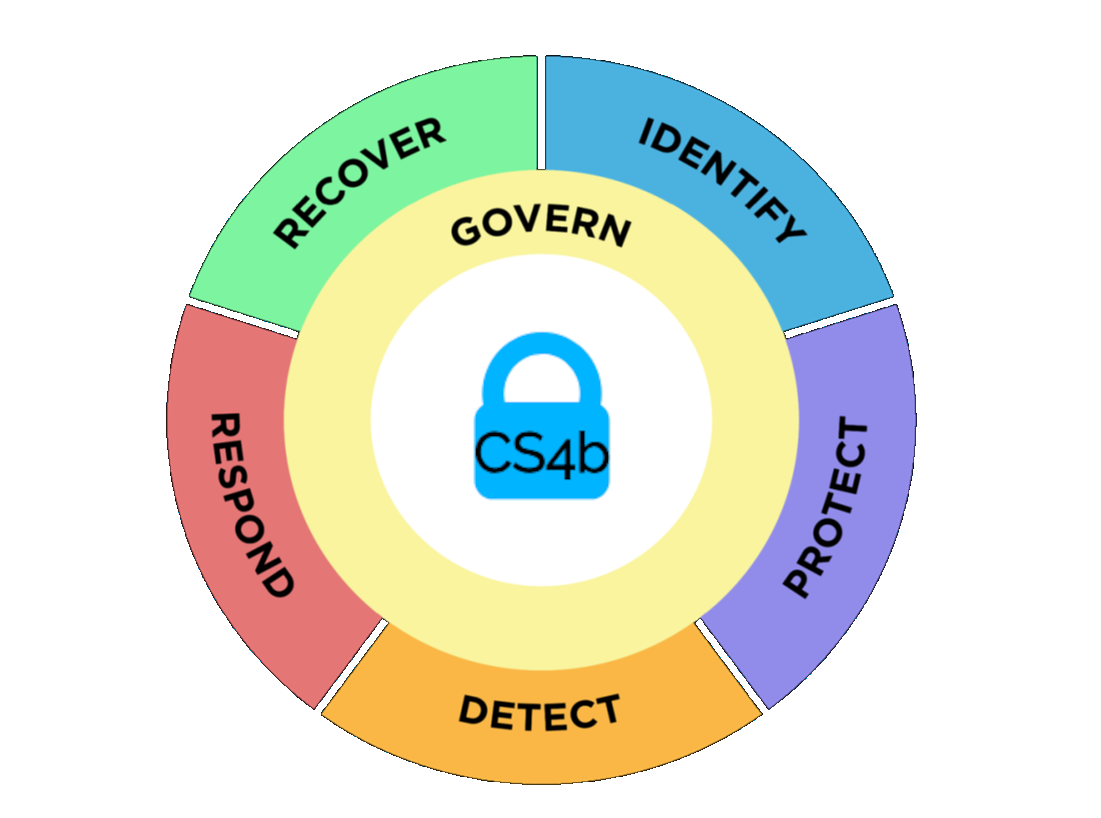
Why NIST CSF 2.0 is Your Perfect Fit
You’ve probably heard about complex cybersecurity frameworks and wondered if they’re just for big companies with giant IT budgets. But the National Institute of Standards and Technology’s Cybersecurity Framework (NIST CSF) is different. It’s not a one-size-fits-all solution; it’s a flexible roadmap that adapts to your business’s size, goals, and resources.
There are no "silver bullets" when it comes to cybersecurity and protecting an organization. For instance, "Zero-day" attacks exploiting previously unknown software vulnerabilities are especially problematic.
However, using the National Institute of Standards and Technology (NIST) Cybersecurity Framework (CSF) to assess and improve management of cybersecurity risks will put your organization in a much better position to identify, protect, detect, respond to, and recover from an attack, minimizing damage and impact.
NIST CSF will enable you to meet or exceed all government mandated cybersecurity regulations like HIPAA, GLBA, PCI-DSS, FINRA, SOX, CMMC, ITSG-33, ISO 27001, and many others.
Not just a software solution, it also uses governance, processes, and awareness
Enable long-term cybersecurity and risk management
A framework that keeps you compliant effortlessly
A framework that is flexible and easily adaptable regardless of size and type of your business
Scalable to grow as your business grows and is a valuable to build trust with your customers
Helps your organization achieve a global standard of cybersecurity
The NIST CSF 2.0 organizes basic cybersecurity activities at their highest level with these 5 functions.
-

Document your assets (hardware, software, people, and critical processes).
Assess the potential impact of a total or partial loss of critical business assets and operations.
Assess cybersecurity risks posed by suppliers and other third parties before entering into formal relationships.
-

Assessment Questionnaire
Identify and control who has access to your business information
Require individual user accounts for each employee.
Create Cybersecurity Policies (HIPAA Security & Privacy, GLBA/IRS WISP, CMMC SSP & POAM, PCI-DSS, Company Cybersecurity Policy)
-

Limit employee access to data and information
Install and activate software and hardware firewalls on all your business networks
Secure your wireless access point and networks
Dispose of old computers and media safely
Train your employees
-

Advanced Threat Security
Email Security and Antispam
Exploit Defense
Full Disk Encryption
Network Attack Defense
Patch Management
Web Content Control
Web Threat Protection
-

Managed Endpoint Detection and Response
Develop Response Plans for disasters, data breaches, and information security incidents
Repair your reputation
Mitigate damages to your customers
Prioritized Alerts Investigation
-

Full backups and incremental backups of important business information and customer data
Consider cyber insurance
Make improvements to processes, procedures, technologies
Business Continuity Plan